Basics of asymmetric encryption
This page contains information on
digital signatures, encryption and certificates within the BTU CA Global
and is primarily intended for interested employees and students of the BTU Cottbus-Senftenberg who are involved in the digital signing of emails and electronic documents and, where applicable, their encryption in their areas of work (or will be involved in the future).
Detailed information for employees and students of the BTU Cottbus-Senftenberg on the subject of ‘certification’ is provided on the IT Services website and is kept up to date.
Encryption and digital signatures
Digital signatures and encryption ensure that
- only authorised persons can view the data intended for them,
- the sender of data can be clearly identified,
- data arrives at the recipient unchanged and any changes can be detected.
Structure of a key pair
PUBLIC KEY:
Public key, accessible to all communication participants.
PRIVATE KEY:
Secret key, remains with the owner of the key pair and is protected by a password (passphrase).
Possible applications:
- Encryption and decryption
- Digital signature
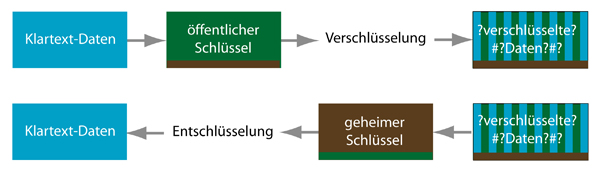
How encryption and decryption work
The sender encrypts a text using the recipient's public key and sends it to the recipient. Only the recipient can decrypt the text using their protected private key.
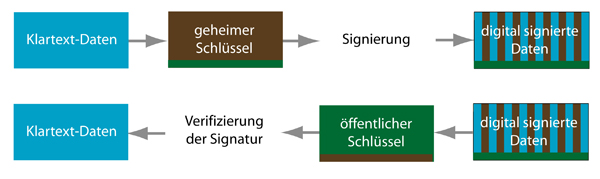
How digital signatures work
The owner of the key signs the data (e.g. the email) with their secret key. The recipient can use the public key to verify the signature and ensure that the person claiming to be the sender of the message is actually the owner of the secret key associated with the public key.
Certificates and tasks of certification authorities
Certificate
Digital signature for public keys. When a certificate is issued, the unique identity of the key holder is verified.
The certificate is a rather long and cryptic digital code or, more clearly, a kind of electronic ID card with a digital signature. The certificate can be used to sign or encrypt emails. A signed email allows the sender to identify themselves to the recipient. It can also be used for authentication, e.g. on the wireless LAN or VPN service of the BTU Cottbus-Senftenberg.
Tasks of certification authorities
- Issuing certificates for public keys
- Verifying the identity of the key holder
- Verifying the public keys for data correctness
- Publishing certificates
- Blocking certificates (if necessary)
- Managing revocation lists
Certification authority at BTU Cottbus – “BTU CA Global”
The operation of the certification authority at BTU Cottbus-Senftenberg (BTU-CA) has been outsourced. The certificates are issued by DFN-PKI. The registration authority (RA) remains at BTU Cottbus-Senftenberg.
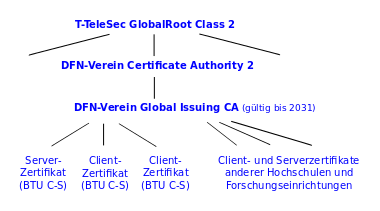
Certification hierarchy
Certification authorities are organised in certification hierarchies.
Structure of the hierarchy in which BTU CA Global is classified